IBRSiQ December 2025
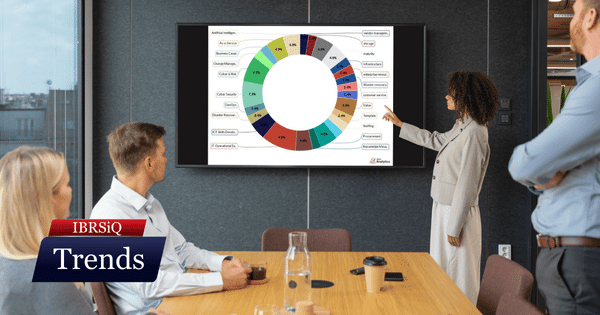
December’s focus shifts toward pragmatic governance, balancing AI adoption and cyber resilience by simplifying processes and prioritising foundational security controls.

December’s focus shifts toward pragmatic governance, balancing AI adoption and cyber resilience by simplifying processes and prioritising foundational security controls.

Most annual trend predictions are little more than marketing disguised as foresight. Market modelling designed to drive consumption rather than economic modelling designed to drive value.
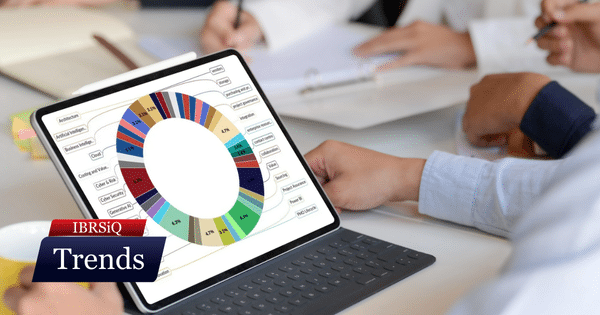
Leaders are prioritising operational optimisation and procurement, whilst navigating AI governance to future-proof their digital strategies.