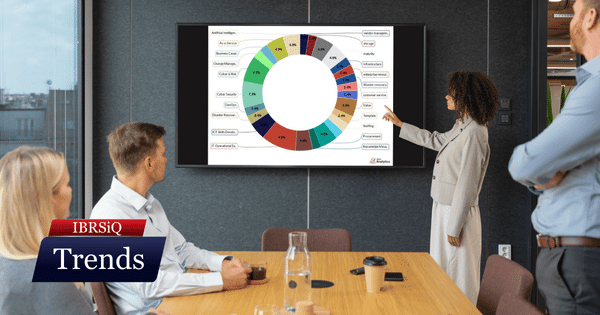
IBRSiQ December 2025
December’s focus shifts toward pragmatic governance, balancing AI adoption and cyber resilience by simplifying processes and prioritising foundational security controls.

December’s focus shifts toward pragmatic governance, balancing AI adoption and cyber resilience by simplifying processes and prioritising foundational security controls.

To build an effective cyber security strategy, organisations must address human manipulation and physical access risks, not just technical controls and training.

Australia’s new Cyber Security Act, effective May 30, 2025, mandates 72-hour incident and ransomware payment reporting for many organisations, shifting cyber security from operational to compliance.

Chinese AI startup DeepSeek’s impressive, low-cost DeepSeek R1 model has drawn scrutiny over data practices and government ties, leading to an Australian ban on February 4, 2025.

Explore how defining and understanding your organisation’s risk appetite is crucial for developing a sustainable and implementable business continuity plan (BCP), ensuring appropriate investment in cyber security, disaster recovery, and business continuity.
SentinelOne’s Purple AI now integrates with major security platforms like Zscaler and Okta, using AI to automate threat detection and response for improved cybersecurity.

Drive successful knowledge management, collaboration and cyber security programs with IBRS whiteboard sessions.

How we authenticate ourselves online is of paramount importance. Traditionally, passwords have been the go-to method, serving as a unique identifier to confirm one’s identity. However, the landscape of authentication has witnessed significant evolution, largely driven by vulnerabilities associated with password-based systems.